TL;DR: The Privacy Revolution — Ethereum’s Next Foundational Shift
Privacy as the default, not an option.
The reason is existential: “whoever has the information — has the power,” and without privacy, decentralization is impossible. Transparent blockchains are broken in the era of AI surveillance, where “cultural tolerance quickly regresses,” and we’re moving toward a world where “AI reads our thoughts.” The crypto community “underestimated privacy for a stupid reason: before Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge (ZK-SNARKs), there was no way to provide privacy in a decentralized manner.”
ZK-SNARKs change everything:
- “Like LEGO blocks for information flow” — users precisely control who sees what
- Privacy Pools — “exclude bad actors without needing backdoors”
- Identity proofs through zero disclosure — users prove uniqueness without revealing identity
- Programmable cryptography — systems compute over encrypted data
Key solutions already work:
- Aztec Network — privacy-first Layer 2 with fully encrypted transactions
- ZKPassport — identity verification without exposing personal data
- Dark Pools — private trading protected from MEV and manipulation
- Privacy Pools — compliance with regulation without compromising privacy
Ecosystem transformation:
- DeFi Renaissance: private transactions eliminate Maximum Extractable Value (MEV) and frontrunning
- New business models: users monetize their data against surveillance capitalism
- Harmony with regulation: cryptographic compliance replaces total bans
- Restoration of digital sovereignty: “the freedom to live without constantly balancing between ‘the private game’ and ‘the public game’”
Ethereum is evolving from a transparent ledger into a trust layer of the internet that preserves privacy, where the end goal is programmable cryptography everywhere.
Vitalik Buterin stated at the Web3Privacy hackathon:
“Today, using privacy protocols requires a separate seed phrase, no multisig support, you need to open a separate wallet, and making a private transfer or withdrawal takes about 5 clicks.”
Ethereum is undergoing its deepest philosophical evolution since launch.
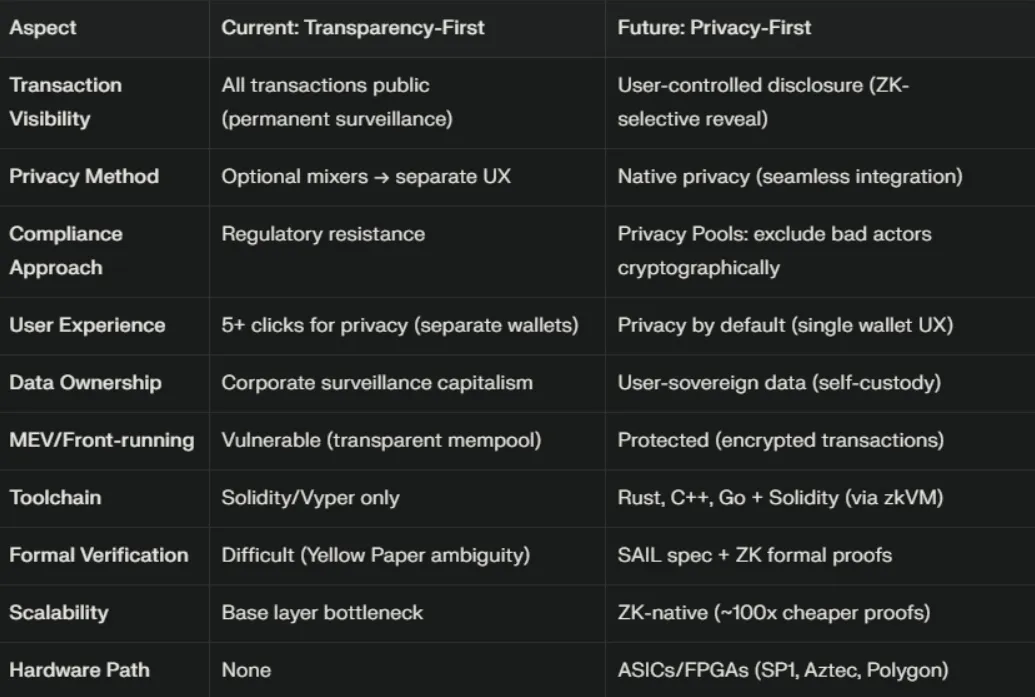
The protocol is no longer gradually adding privacy features — it’s fully re-architecting its approach to user sovereignty, shifting from “transparency by default” to “privacy by default.”
This initiative creates a “Private Ethereum” — a systemic rethinking of the protocol based on three key pillars:
- Private consensus (validators hide actions)
- Private data (the protocol encrypts mempool and state)
- Private execution (smart contracts run with native ZK privacy)
At the heart of this transformation lies one fundamental question:
Is Ethereum’s transparent architecture — the one that created the DeFi revolution — now blocking the path to true financial sovereignty?
https://hackmd.io/@pcaversaccio/ethereum-privacy-the-road-to-self-sovereignty
Researcher Pascal Caversaccio from the ETH Research community articulates the long-term vision:
“Privacy must be the network’s default state — not an option the user has to manually enable.”
For years, this remained “an unattainable dream” because one key element was missing — the concept of real-time in programmable cryptography:
ZK-SNARKs operate inside familiar user processes, without separate wallets or complex User Experience (UX) flows.
Now zero-knowledge proof in real time works. The theoretical limitations of Ethereum’s transparent architecture have turned from a philosophical debate into practical bottlenecks blocking mass adoption.
This analysis explores the technical and philosophical arguments in favor of Ethereum’s migration to privacy-by-default infrastructure — a transformation that:
- unlocks true financial sovereignty
- eliminates surveillance capitalism from Web3
- returns Ethereum to its core mission — to build “unstoppable applications” that protect user autonomy, not expose them to control by corporations and the state.
Dress Code Is Changing: From Nudist Beach to Masquerade
The current architecture of Ethereum is built on a transparency-by-default model, where every transaction, balance, and smart contract interaction is publicly visible on-chain. This model enabled trusted and verifiable systems that gave rise to DeFi and Non-Fungible Token (NFT) ecosystems. However, radical transparency has turned into a fundamental “privacy debt,” threatening user sovereignty in the age of AI surveillance and corporate data extraction.
Privacy-by-default Ethereum is not a single feature but a systemic architectural philosophy — a full “privacy stack” that completely rethinks how users interact with the blockchain.
Vitalik Buterin’s privacy roadmap lays out key principles for achieving true financial sovereignty:
- Programmable Disclosure
The foundational privacy model assumes zero information leakage by default — users themselves choose what to reveal and to whom.
Vitalik emphasizes: ZK-proofs work “like LEGO blocks for information flow,” providing granular control over data visibility instead of the current “all-or-nothing” model.
- Modular Privacy
Different privacy levels are layered through composable cryptographic protocols.
This allows building a simple base layer (e.g., regular ZK-transactions) and expanding it with advanced features (Privacy Pools, identity proofs) without overloading the user experience with unnecessary complexity.
- Inherited Compliance
The new model builds on mature regulatory compliance frameworks, including Privacy Pools and ZK-compliance proofs.
Pascal Caversaccio notes:
“Ethereum will get regulatory approval for free, instead of fighting regulators in a confrontational mode.”
The Naked Truth About Power: Whoever Watches, Rules
“Privacy is an important guarantor of decentralization: whoever has the information, has the power — so we must avoid centralized control over information.”
[ Vitalik Buterin ]
Blockchain transparency, originally envisioned as a tool for financial democratization, has turned into a mechanism for concentrating informational power. When every transaction, balance, and smart contract interaction is visible to all network participants, an asymmetry of capabilities emerges:
MEV bots and institutional players gain advantages. They analyze public transactions in real time and extract profit through front-running and sandwich attacks. Research shows: MEV extraction reaches $700 million annually — regular users pay this tax to the technologically advanced.
Corporations and governments track citizens’ financial flows with unprecedented granularity. Vitalik notes: “When people in the real world express concern about centrally managed technical infrastructure, sometimes it’s about operators unexpectedly changing the rules… but just as often, it’s about data collection.”
The social and economic consequences intensify. What we get is not a decentralized financial system, but a sophisticated form of surveillance capitalism.
The Architect of Digital Veils
Aztec Network acts as a pioneer in solving a fundamental contradiction.
The Aztec team has developed a privacy-first Layer 2 solution that preserves the advantages of Ethereum decentralization and eliminates problems of informational asymmetry.
Key innovations of Aztec:
- Private Execution Environment (PXE): executes all private functions locally on the user’s device, generates ZK-proofs, and never discloses secret information to external servers
- Hybrid State Model: a unique architecture — the private state uses a UTXO model with encrypted notes, the public state works like Ethereum. Developers choose the level of privacy for each aspect of the application
- Noir Programming Language: a Rust-like DSL that allows developers to write ZK circuits without knowing cryptography. Electric Capital notes: Aztec ranked first in growth of full-time developers in 2023
- Native Account Abstraction: every account in Aztec is a smart contract with customizable authorization, supporting gasless transactions, multisig wallets, and alternative signature schemes
Aztec CEO Zac Williamson formulates the project’s philosophy:
“Privacy is the missing link needed to unlock the full potential of blockchain.”
The team goes further — Williamson explains:
“Currently, we treat blockchain privacy as an ‘all or nothing’ principle.”
Aztec proves a revolutionary idea: true decentralization requires programmable privacy.
Informational power is returned to users, not concentrated in the hands of technological elites.
This is an architectural shift from “transparency by default” to “privacy by choice.”
The Problem of Personal Freedom
“Privacy gives you the freedom to live in the way that best suits your personal goals and needs — without having to constantly balance between the ‘private game’ (your own needs) and the ‘public game’ (how other people will perceive and respond to your behavior).”
[Vitalik Buterin]
The problem of identity verification has worsened.
Traditional Know Your Customer (KYC) systems require users to fully disclose personal data: full name, address, date of birth, passport number, photos.
ZKPassport founder Michael Elliot notes:
“You rely on third parties for the security of your data, but often something goes wrong… they send confidential documents by email to the wrong people.”
The economic consequences of transparency are intensifying.
Companies use personal data for dynamic pricing and to manipulate consumer decisions.
Vitalik warns:
“The more a company knows about you, the more opportunities it has to offer you a personalized price that maximizes how much it can extract from you.”
Social coercion through digital profiles creates a “panopticon” effect
https://www.moyak.com/papers/michel-foucault-power.html
where people self-censor, assuming constant surveillance.
Users lose the ability to experiment with identity, explore new interests, or express unpopular opinions without fear of future consequences.
Dance of the Seven Veils for KYC
ZKPassport revolutionizes the approach to identity verification and returns control over data to users.
The ZKPassport team has created a solution that proves the necessary facts about the user without disclosing excessive information.
Co-founder Michael Elliot explains:
“What if you could disclose only what you really need to disclose for a specific service… if you need to disclose only your country and nothing more, then that is all you need to disclose.”
Key innovations of ZKPassport:
- Selective disclosure: users prove age over 18 without revealing exact date of birth
- Client-side proof: the user’s smartphone generates all ZK-proofs locally — “All personal data… never leaves the smartphone”
- Government signature: the system uses cryptographic signatures in biometric passports as decentralized anchors of trust
The philosophical meaning of the approach goes beyond technical improvements.
A digital identity researcher formulates:
“Self-sovereignty here is the concept of individual control over personal data relating to identity.”
ZKPassport returns to users digital sovereignty — the ability to control what information about them is available and to whom.
The technology restores true personal freedom in digital space:
users live, explore, and interact online without constant fear of ‘what other people will think’.
ZKPassport proves: technology serves the liberation of the human, not enslavement — the true mission of decentralized technologies.
Programmable privacy initiates the transition from “constant self-censorship” to “authentic digital existence.”
Privacy Pools: Regulatory Harmony Through Math
Privacy Pools — the evolution of cryptocurrency mixers, created by Vitalik Buterin as a compliance-friendly alternative to Tornado Cash after its sanctions in 2022.
Main innovation: users prove honesty without revealing identity through ZK-proofs.
When withdrawing funds, the system generates cryptographic confirmation that the deposit DOES NOT belong to a list of known hacks or sanctioned addresses.
Criminals physically cannot create such proof, while honest users receive a mathematical guarantee of privacy with regulatory compliance.
Privacy Pools use Association Sets — dynamic lists of “clean” deposits, maintained by independent curators.
Users choose their own level of strictness: from liberal filters (excluding only obvious criminals) to strict requirements of institutional investors.
Vitalik personally tested the system with the first deposit in March 2025, proving: programmable privacy allows tuning the balance between anonymity and regulatory compliance.
Hunting the Naked Whale: Why Trading Requires Darkness
A Dramatic Case of Blockchain Transparency
The story of James Wynn has become a symbol of the fundamental problem of transparent blockchains:
when everyone sees your cards, you are doomed to lose.
In May 2025, anonymous trader Wynn lost $97 million in a series of liquidations on the decentralized exchange Hyperliquid.
Crypto analytics platform Lookonchain recorded the mechanism of the disaster:
other traders could see Wynn’s every position in real time and traded against him.
One trader made $5.6 million in three days simply by opening opposite positions — selling when Wynn bought, and vice versa.
In traditional finance, this is called “whale hunting” — smaller participants team up to forcefully liquidate a large player using information about their positions.
The Dark Forest of Ethereum
This story illustrates what Paradigm researcher Dan Robinson called the “dark forest of Ethereum” — an environment where public disclosure of location is equivalent to instant destruction.
Robinson encountered the same problem while trying to rescue $9.6 million from a vulnerable smart contract.
His team couldn’t send the transaction to the mempool — bots would steal it instantly.
Robinson described the Ethereum mempool as a place where:
“The apex predators take the form of arbitrage bots. If the chain itself is the battlefield, then the mempool is worse: a dark forest… public disclosure of location is equivalent to instant destruction.”
The Wynn story is the dark forest in action.
Only instead of mempool bots, predators were watching his positions directly on the exchange.
Robinson warned:
“Without neutral, public infrastructure for extracting MEV, MEV risks becoming an insiders’ game.”
Wynn became the victim of exactly such a game.
Source: https://www.paradigm.xyz/2020/08/ethereum-is-a-dark-forest
Statement by CZ and the Need for a Solution
The situation with James Wynn drew the attention of influential figures in the crypto industry.
Former Binance CEO Changpeng ‘CZ’ Zhao publicly called for the creation of a “dark pool perp DEX” after Wynn’s massive losses:
“It leads to increased slippage, worse prices, and higher costs for you” — he commented on the problems of transparent DEXs, where
“Every trader can also see all positions and liquidation points happening in real time.”
CZ emphasized the fundamental issue:
“If you want to execute a $1 billion order, you definitely need to get it done before the market sees it.”
The public nature of positions turns large traders into “big red targets” for manipulation and MEV attacks.
Key Principles of the Dark Forest
- Invisible execution: “The only way to be safe is if no one sees you.”
Transactions must remain hidden until execution. - Coordination with miners:
Users need private channels with miners to bypass the public mempool. - Systemic threat:
MEV creates an “existential risk to the security of Ethereum’s consensus” through incentives for block reorganizations. - Insiders’ game:
Robinson warned:
“Without neutral, public infrastructure for extracting MEV, MEV risks becoming an insiders’ game.”
Dark Pools Solve the Problem Radically
Dark pools completely remove transactions from the public mempool.
Instead of sending orders to a place where “public location disclosure is equivalent to instant destruction,” dark pools create encrypted channels:
- Trading intents are processed off-chain
- MEV bots can’t see transactions
- Frontrunners can’t attack invisible targets
From Insiders to Democratization
Problem: Traditional solutions required personal connections with miners.
MEV turned into a game for the chosen few.
Dark pools democratize protection:
- Any user gains access to private trading
- Personal connections with miners are no longer needed
- Programmable privacy replaces trust-based solutions
- P2P matching eliminates intermediaries
Inversion of MEV Dynamics
Before: Predators extract value through informational asymmetry.
After, through dark pools:
- Order flow auctions: users receive compensation for extracted value
- Competitive bidding: searchers compete for the right to process the order, increasing the price for the user
- Value return: instead of “certain death,” users receive a fair share of MEV
Philosophical Shift
Robinson dreamed of a “permissioned, transparent, and fair MEV extraction ecosystem.”
Dark pools implement this vision:
- Permissioned: anyone uses private trading
- Transparency: executions are verified onchain through ZK-proofs
- Fairness: MEV revenue is distributed among users, not concentrated in bots
A shift is happening — from “the only way to be safe is if no one sees you” to “everyone has the right to invisibility by default.”
Dark pools turn individual protection (finding a miner) into a systemic guarantee (architectural privacy).
Regular users gain protective mechanisms previously available only to insiders.
The End of the Forced Striptease Era

A New Perception of Data
Users are experiencing a fundamental transformation of consciousness.
Data is turning from “something corporations take for free” into “digital property under my control.”
Users have full legal ownership of their data… just like when you park your car in a parking lot, the parking lot doesn’t own your car.
Consumers are willing to share data for rewards — but now consciously and on their own terms, not as a “price of entry” into digital services.
From Trust in Institutions to Trust in Math
Programmable privacy creates a new mental model: “Trust is replaced by cryptographic certainty.”
Users no longer hope that corporations “won’t misuse” their data. ZK-proofs provide mathematical guarantees of privacy.
This is a philosophical shift — from belief in good intentions to cryptographic assurance.
Conscious control:
Instead of “agree to everything and forget,” users move to strategic privacy management.
Every disclosure of information becomes a deliberate decision.
The Cultural Shift of the Era
Programmable privacy initiates the transition from “digital slavery” to “digital sovereignty.”
Users stop being the product sold to advertisers and become sovereign agents defining the terms of interaction.
This is a pivotal moment of the digital age — humanity takes back control in the digital space and asserts: technology must serve human autonomy, not undermine it.

